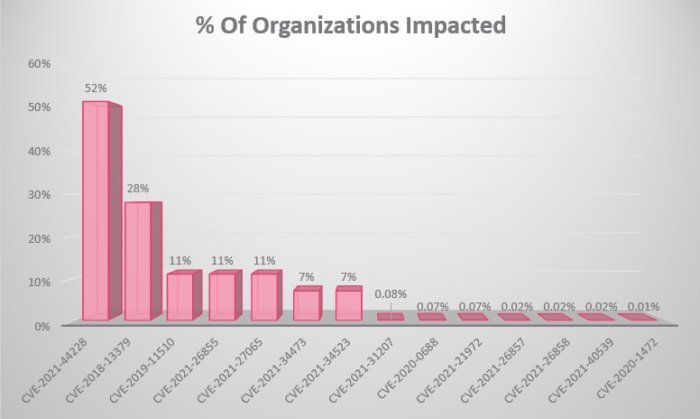
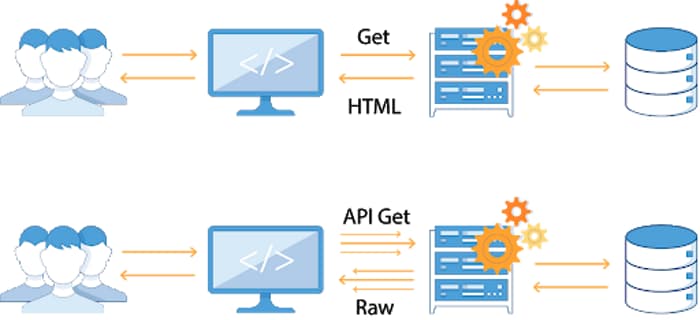
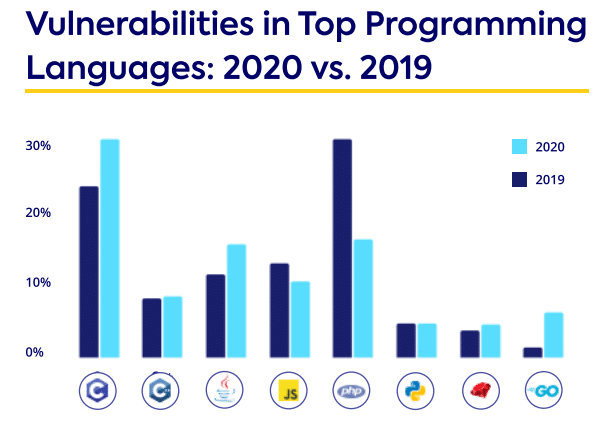
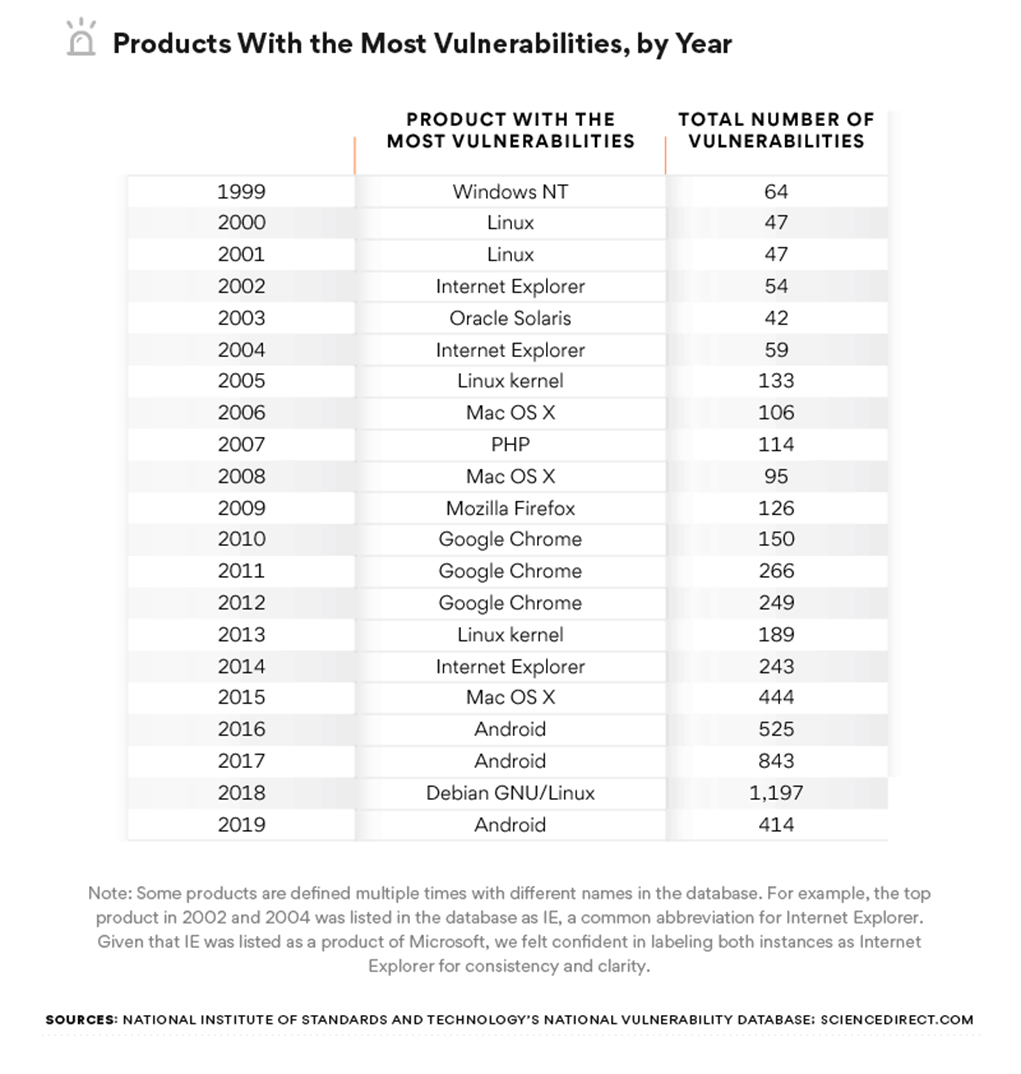
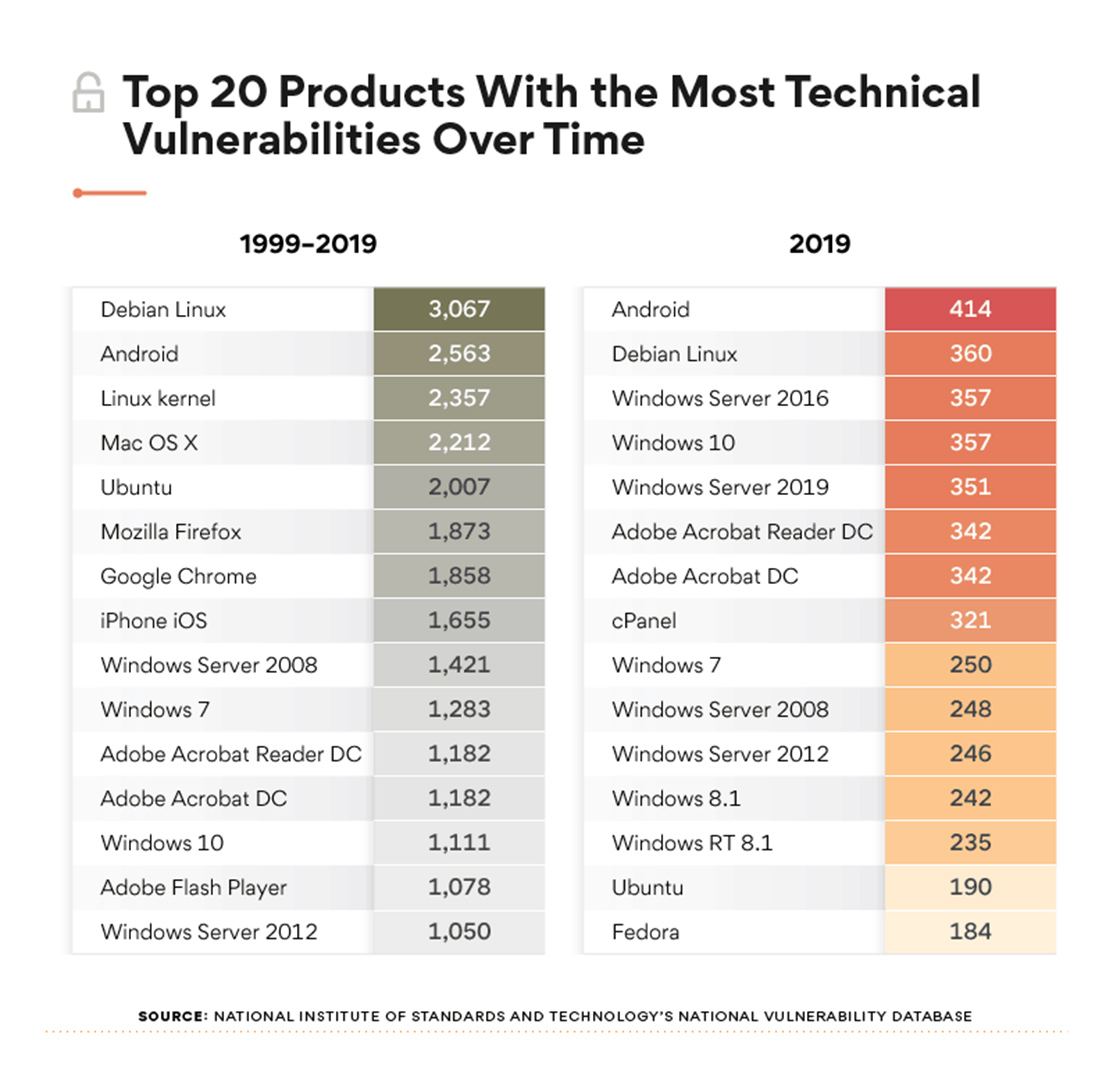
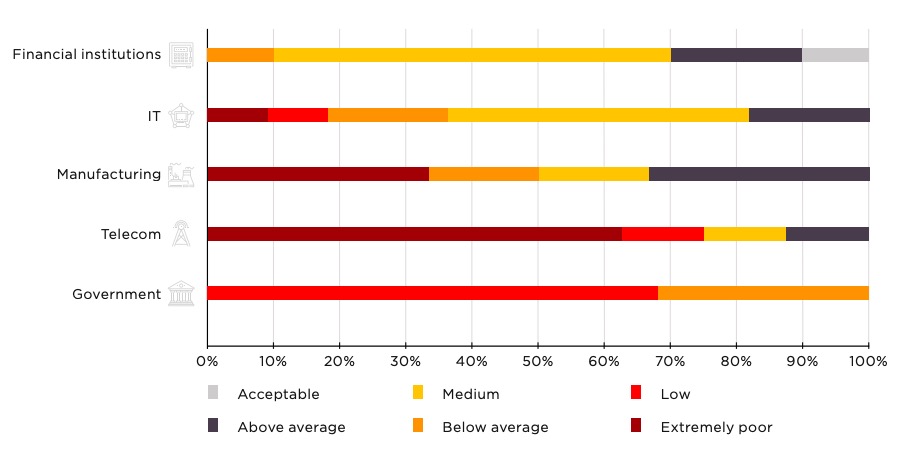
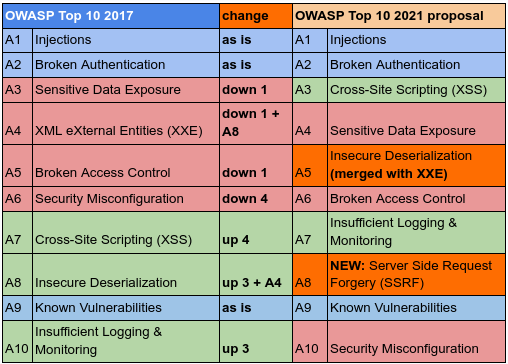
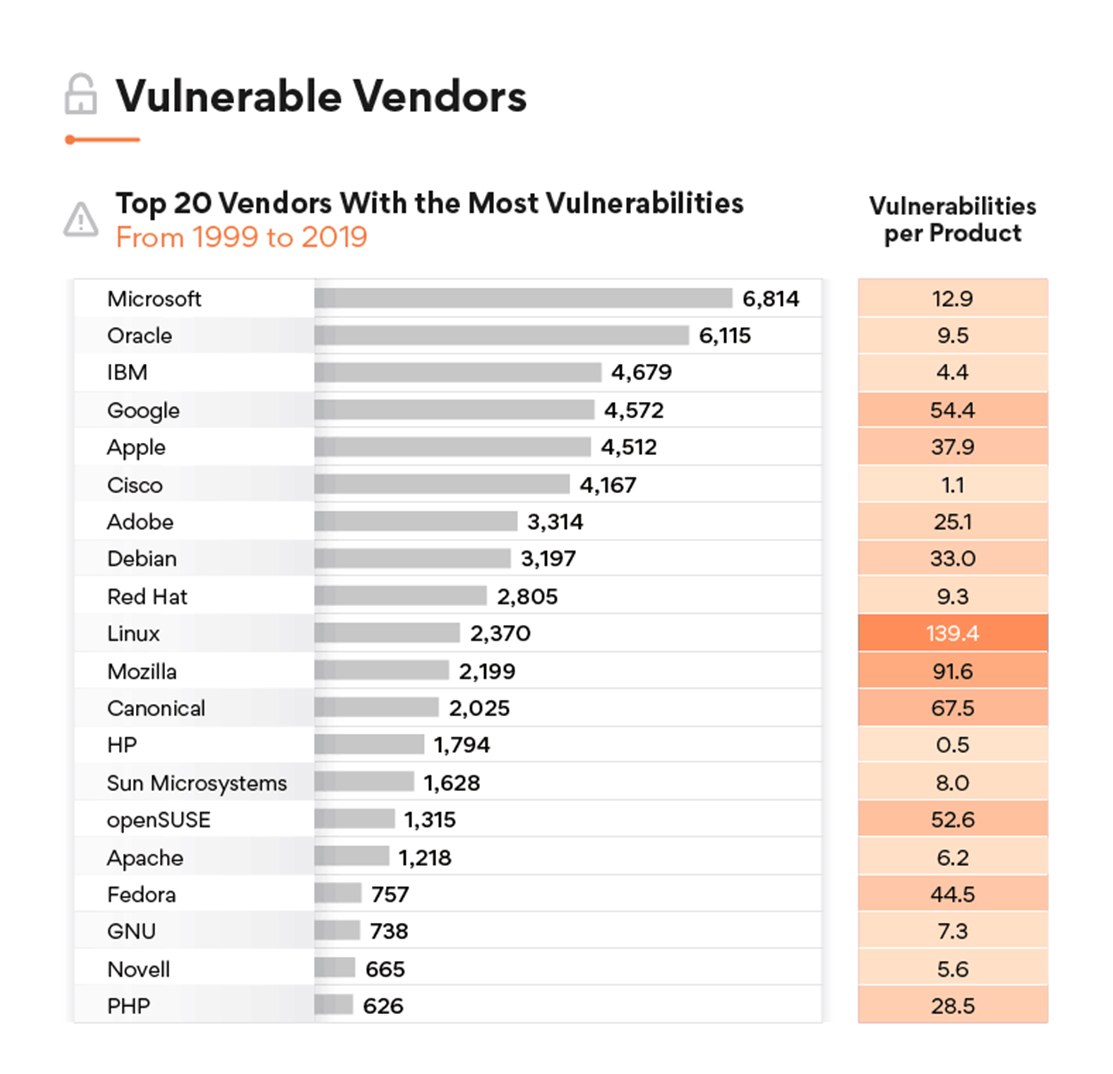
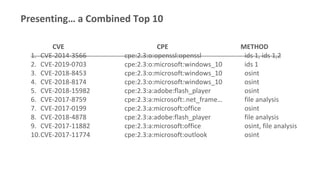
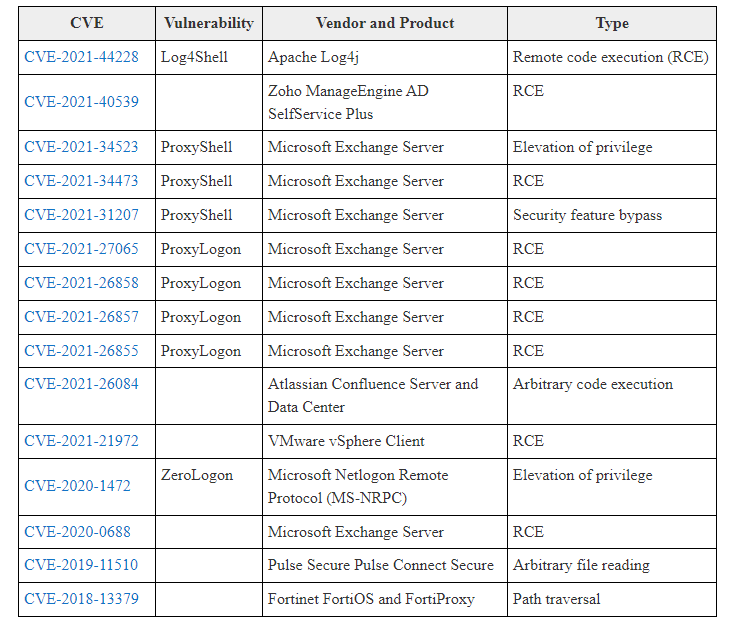
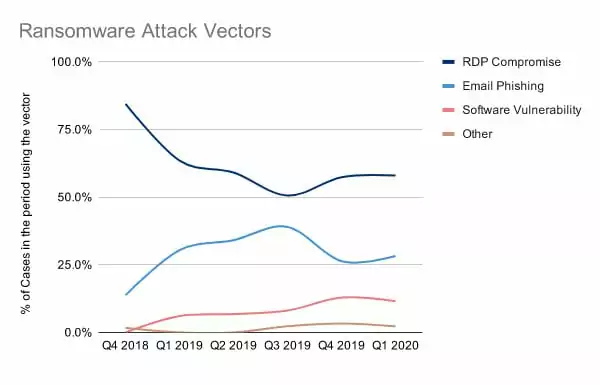
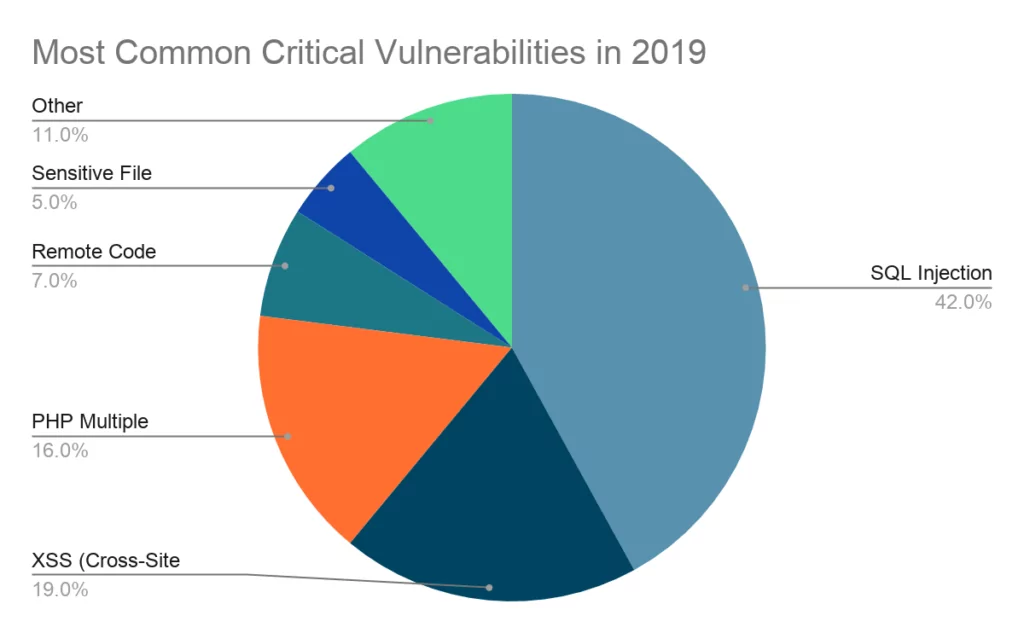
The top five vulnerabilities that could lead to a cyberattack | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More

2019 Cybersecurity Insights -4 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.