Web Security and the OWASP Top 10: The Big Picture - Paperpicks Leading Content Syndication and Distribution Platform

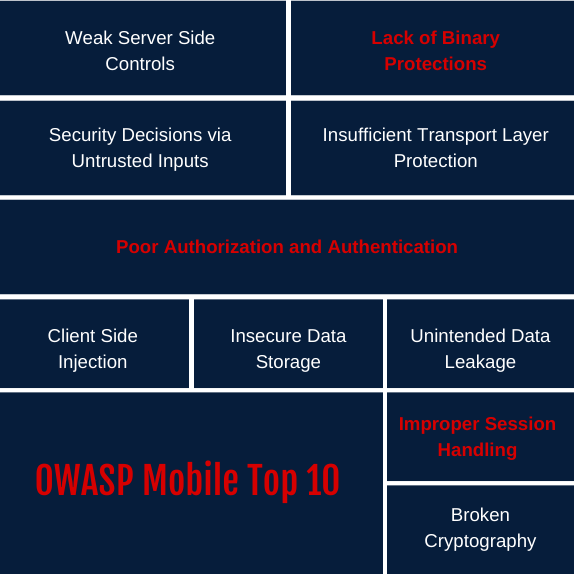
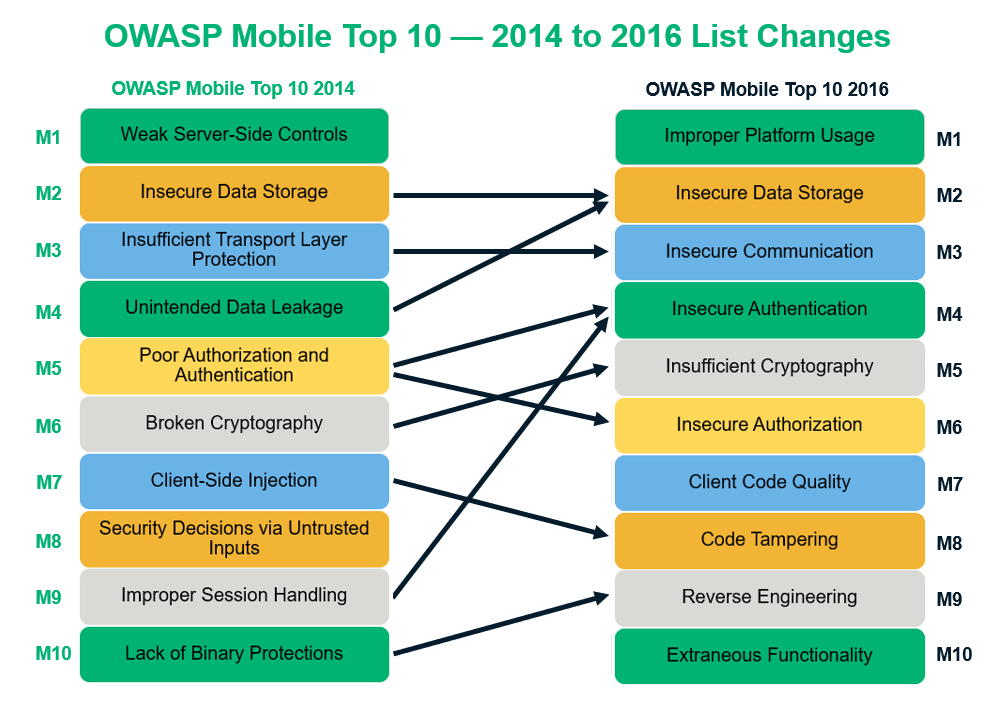
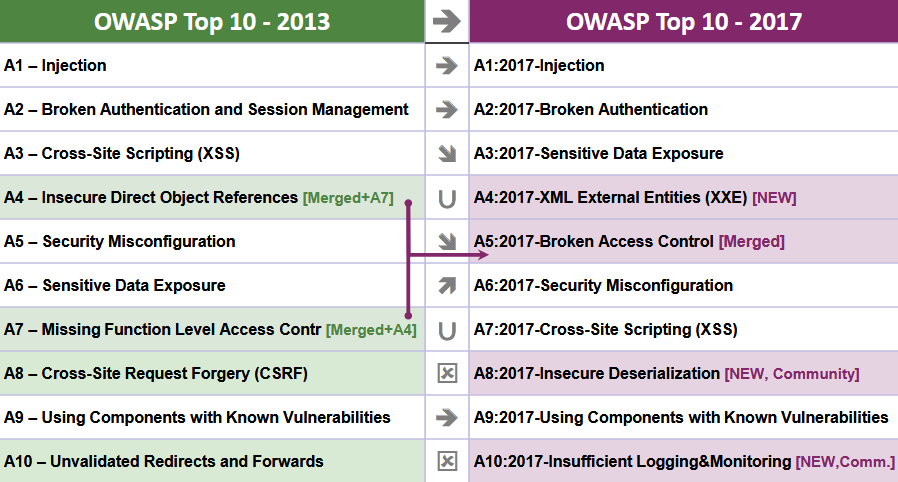
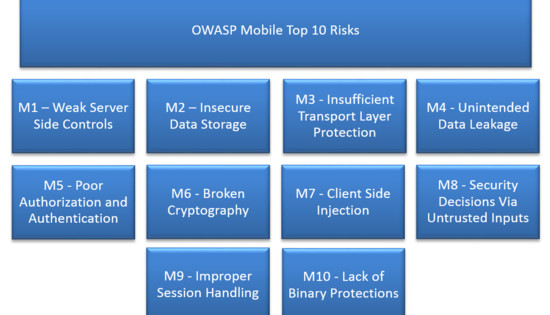
Why OWASP Top 10 (web application) hasn't changed since 2013 but Mobile Top 10 is as recent as 2016? - Information Security Stack Exchange