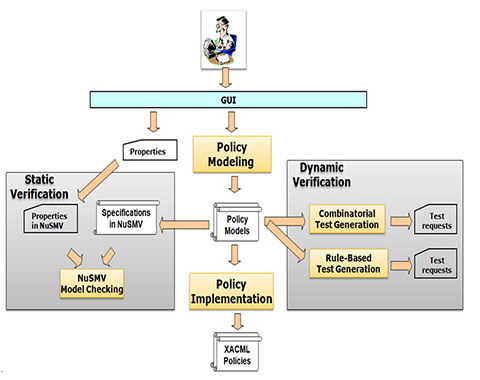
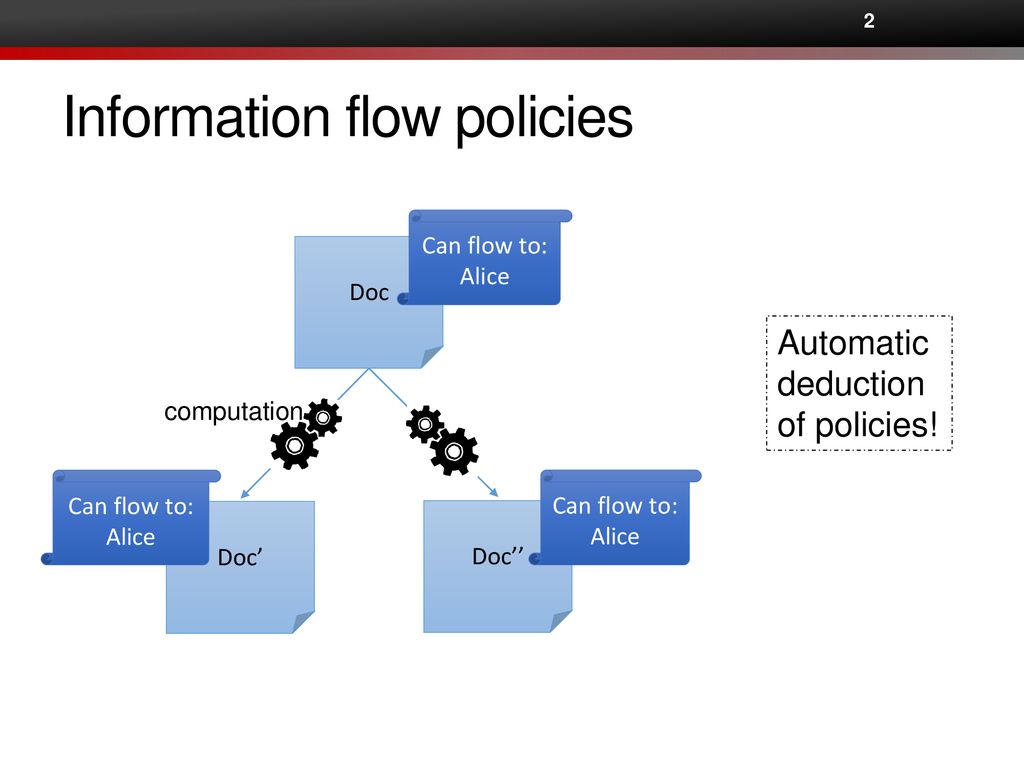
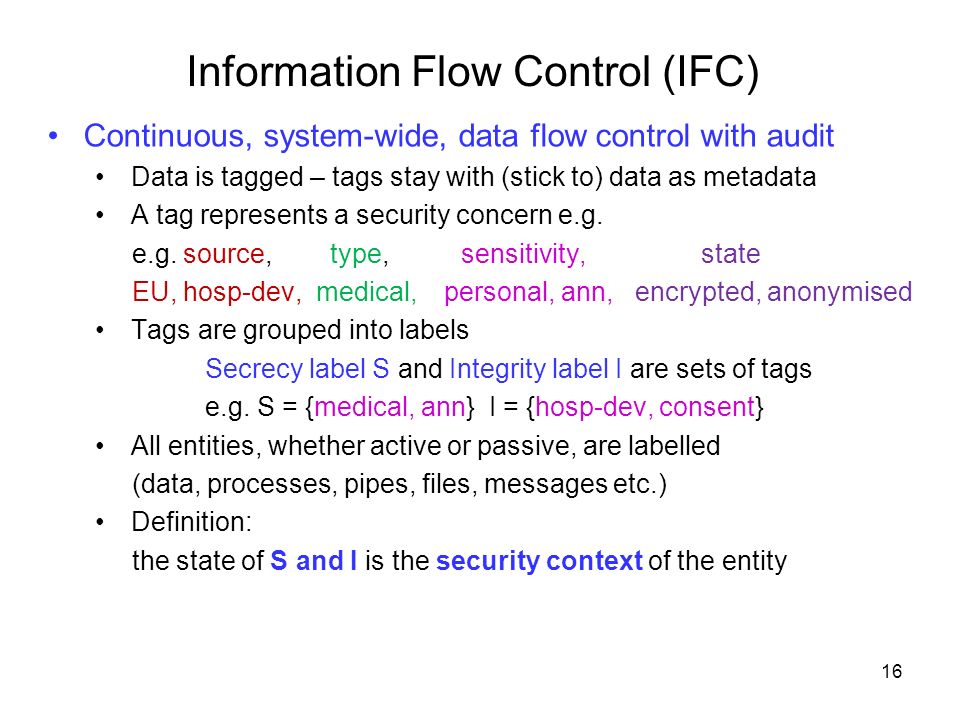
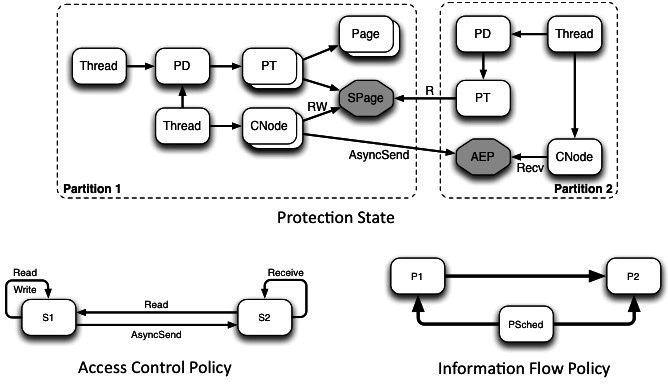
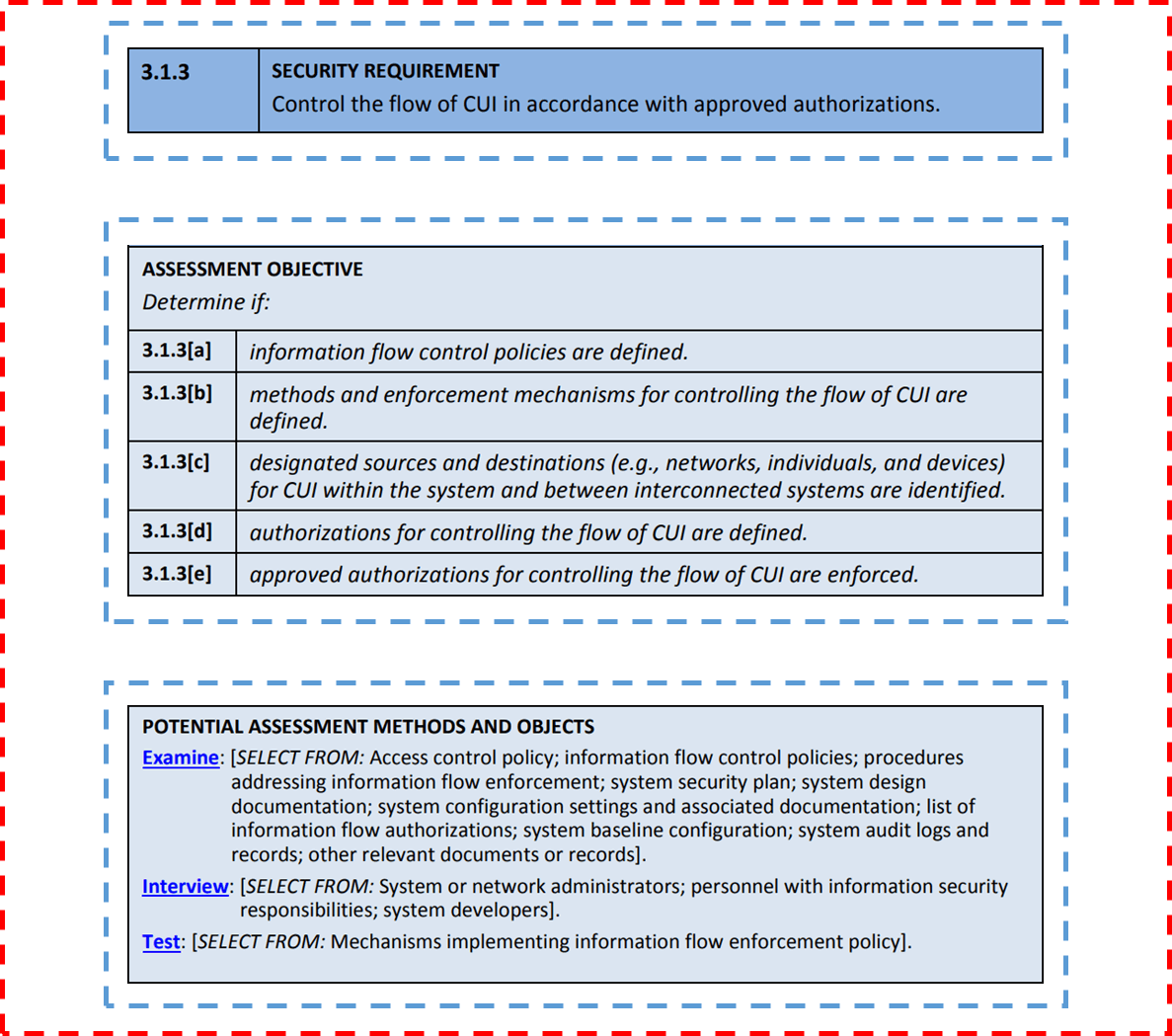
Information Flow Based Security Control Beyond RBAC: How to enable fine-grained security policy enforcement in business processes beyond limitations of role-based access control (RBAC) | SpringerLink

The data flow diagram for an example of logic of the control policy... | Download Scientific Diagram

Method for tenants to jointly formulate information flow control strategy. | Download Scientific Diagram
Defining an Information Flow Control Policy with Declassification and Countermeasures - Archive ouverte HAL

Runtime Verification of Information flow: Policy-Based Runtime Verification of Information Flow Control: Sarrab, Mohamed Khalefa: 9783845432748: Amazon.com: Books