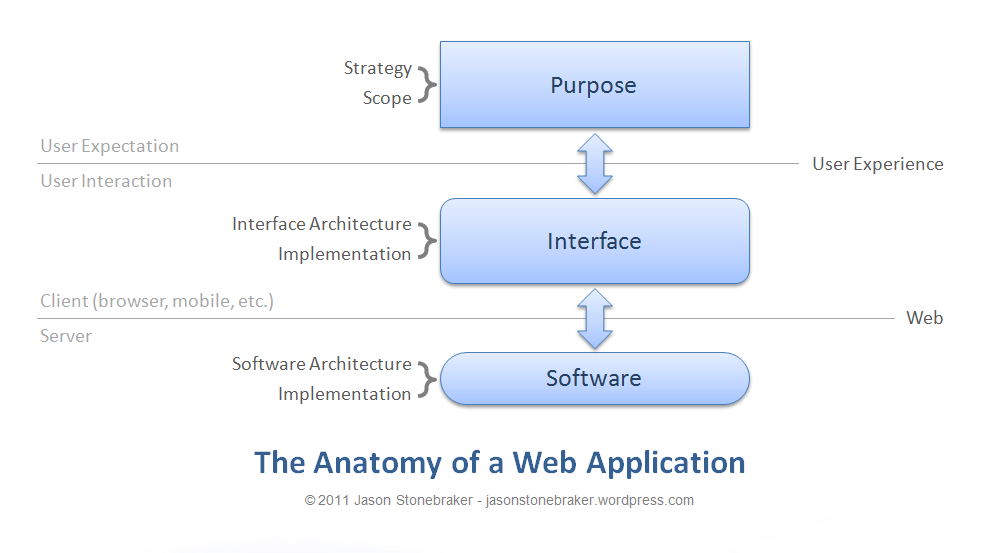
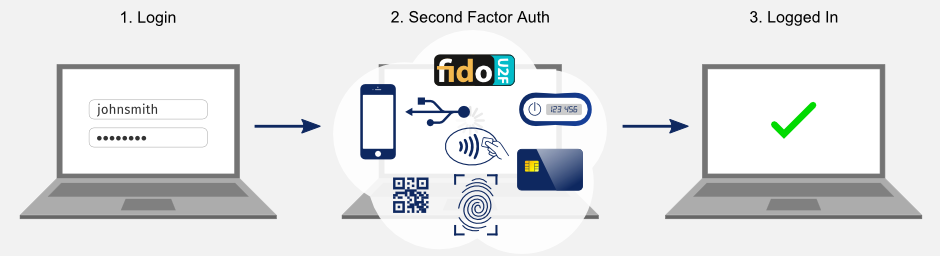
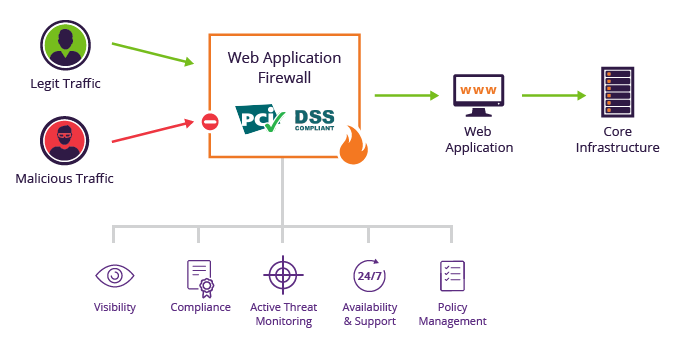
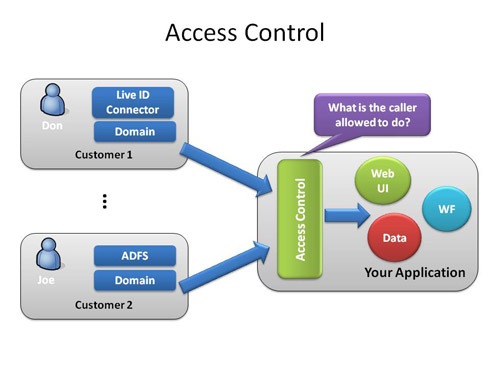
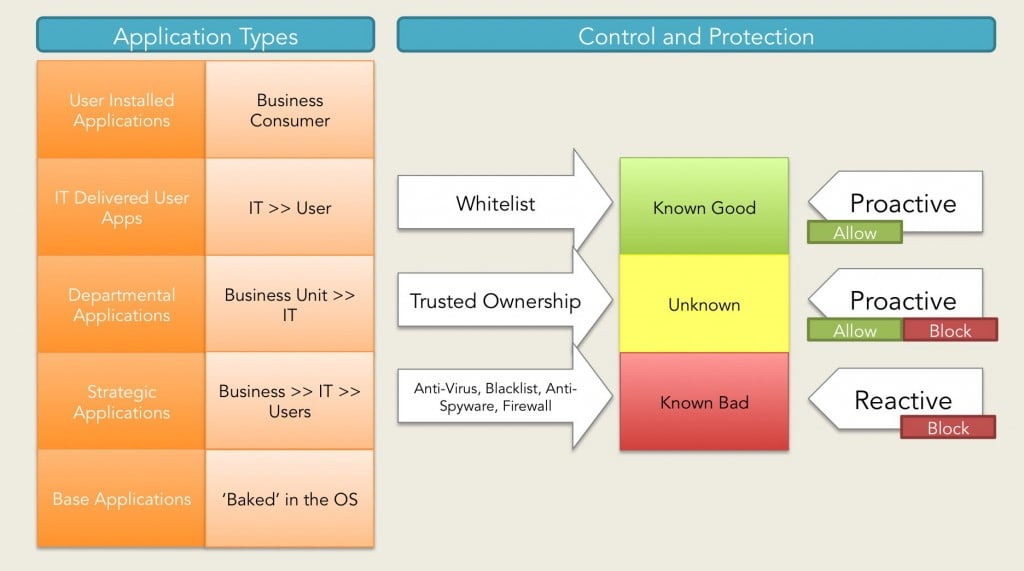
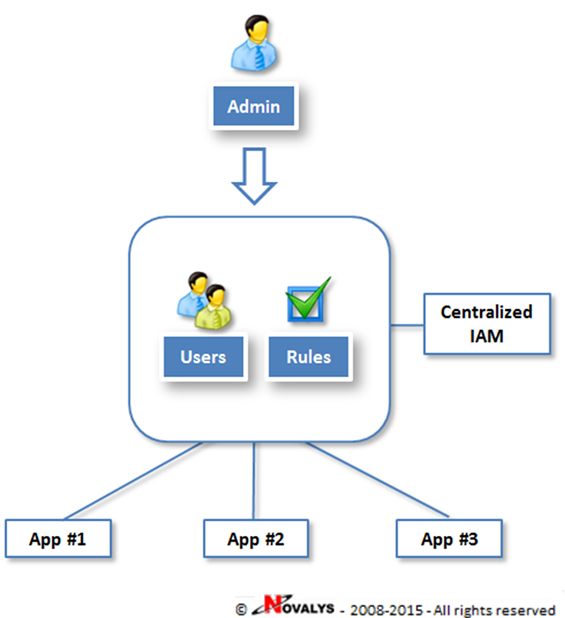
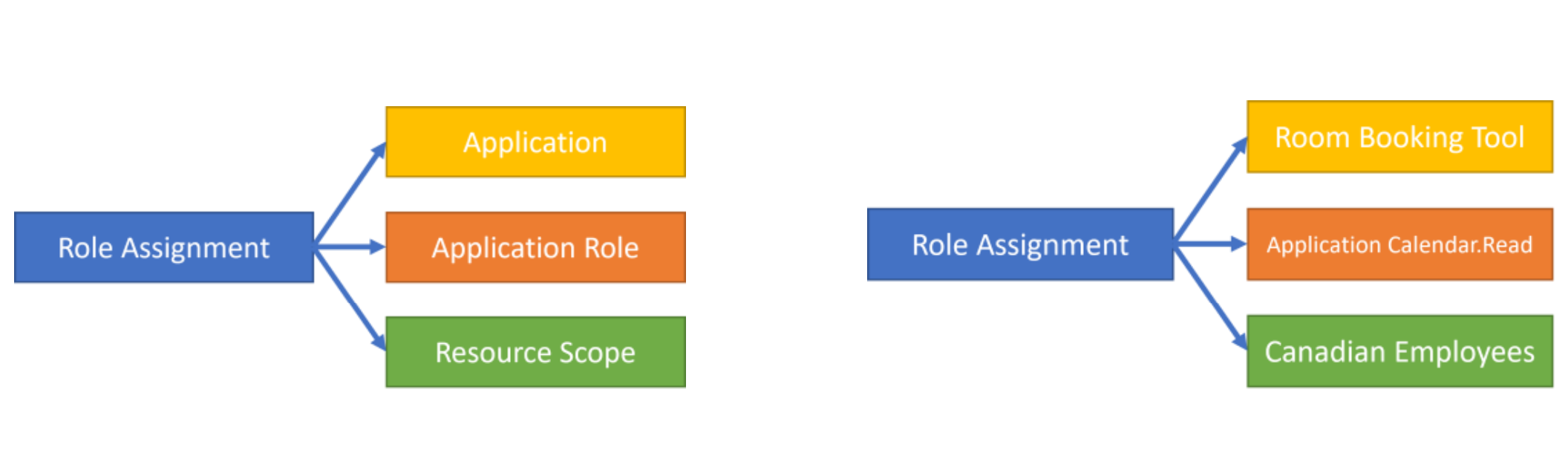
How to design access control system for Saas application | by Anna Savytska | Muzli - Design Inspiration
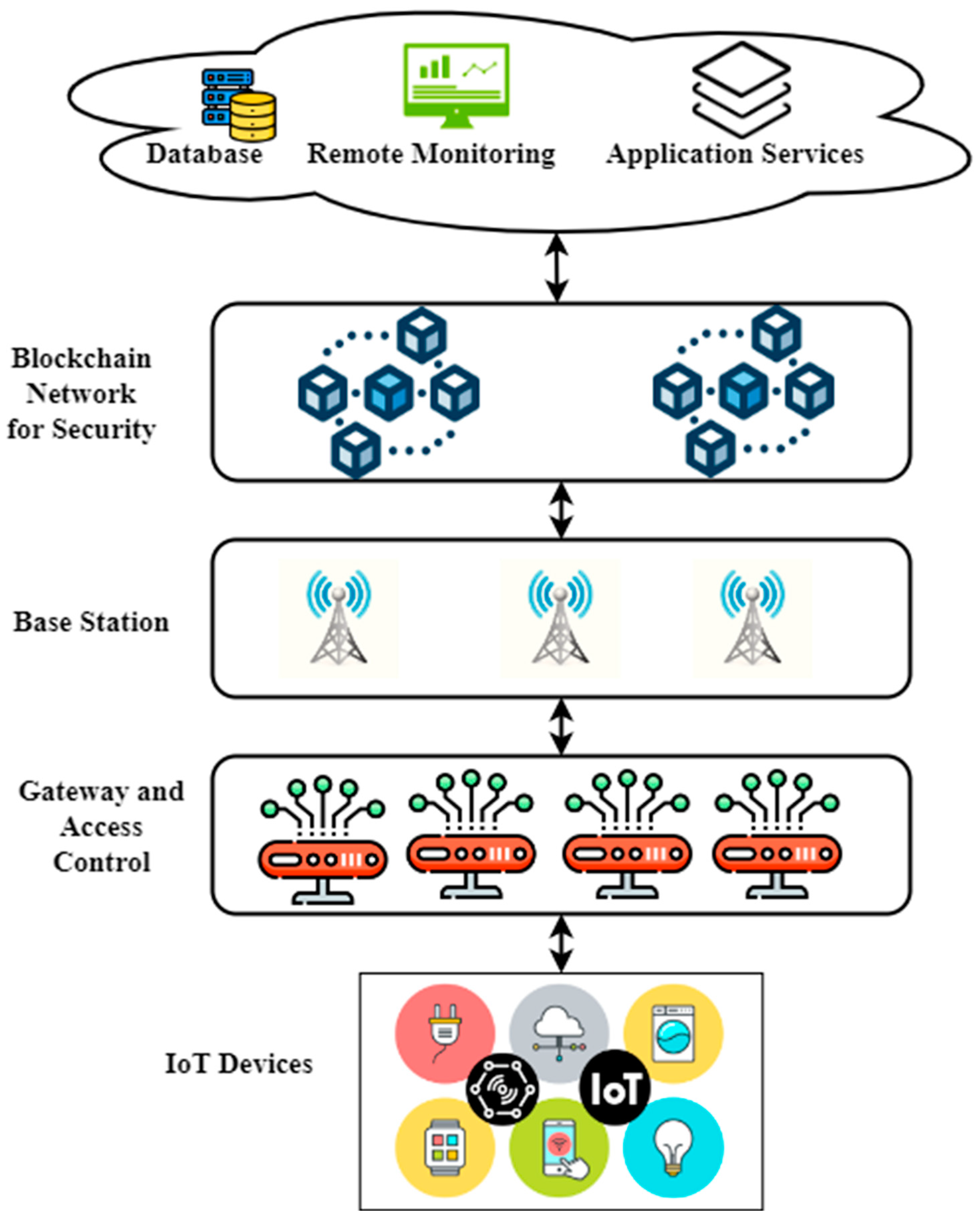
Sensors | Free Full-Text | Applying Access Control Enabled Blockchain (ACE-BC) Framework to Manage Data Security in the CIS System
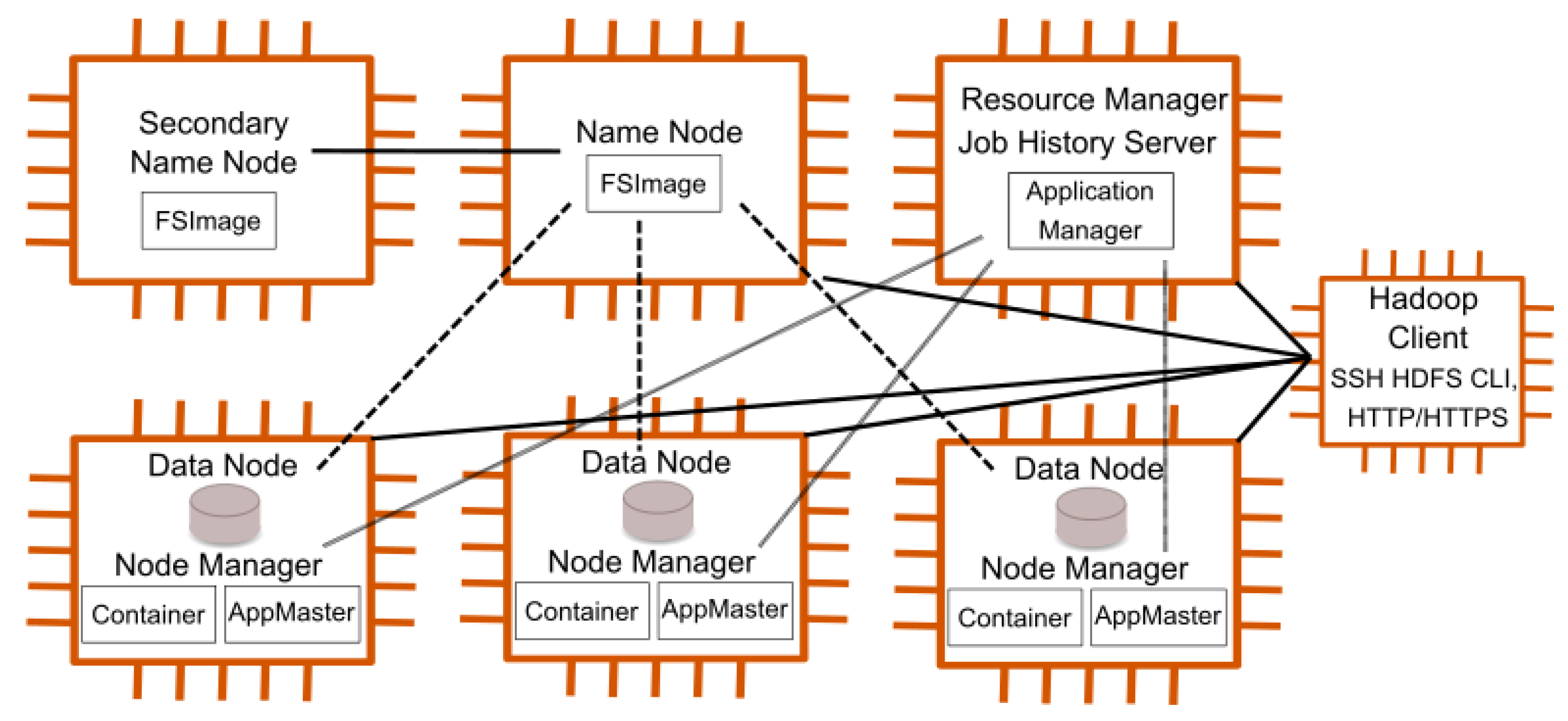
Applied Sciences | Free Full-Text | A Framework for Attribute-Based Access Control in Processing Big Data with Multiple Sensitivities